For their work to ensure that information on mainstream mobile devices can be stored securely and deleted permanently, Bo Chen and Niusen Chen have been honored with Michigan Tech’s 2024 Bhakta Rath Research Award.
Michigan Technological University cybersecurity expert Bo Chen and his graduate student mentee Niusen Chen, as well as the researchers who collaborated with them, are the first to develop the capability for plausibly deniable encryption (PDE) for everyday computing devices. The breakthrough was achieved through careful consideration of the unique software and hardware components in the electronic devices that many of us regularly use. These include flash storage and security architecture such as TrustZone, the latter of which is designed to isolate and protect sensitive information stored on a device.
About the Award
The Bhakta Rath Research Award, founded in 2010, is presented to a graduating Michigan Tech Ph.D. student and faculty advisor “who have done something valuable for American industry and society,” encouraging faculty and doctoral students to conduct research that meets the nation’s needs and the challenges of emerging technologies.
Bo Chen is an associate professor of computer science in the Michigan Tech College of Computing. The director of Tech’s Institute of Computing and Cybersystems Cybersecurity Center, he served as advisor to Niusen Chen, who completed his Ph.D. in computer science under a finishing fellowship in 2023 and is now a research assistant professor at MTU.
PDE goes beyond protecting data. It hides the data’s existence, even in situations where the decryption key is leaked. PDE systems are considered increasingly important as more and more people store sensitive information on their mobile devices.
Researchers also confirmed and addressed the possibility that sensitive data remnants can exist within flash storage and be resistant to conventional secure deletion techniques. They created what they describe as a “fresh secure deletion capability for mobile devices that meticulously manages these remnants, guaranteeing the complete and irreversible removal of confidential information from mobile devices.”
Who is Bhakta Rath?
The Naval Research Lab named a room after him. The more than 750 team members he led include Nobel laureates. He’s received three honorary doctorates. And it all started at Michigan Tech. Learn more about Bhakta Rath’s personal and professional story.
In a letter of support for Bo Chen and Niusen Chen’s nomination, Weisong Shi, who has collaborated with the duo since 2019 on the National Science Foundation-funded project, said their research will “greatly contribute to national security efforts, given the high demand for secure data deletion in critical sectors, including federal agencies.”
“Its practical applications are extensive, ranging from safeguarding personal data to securing critical information for organizations and government agencies,” said Shi, who is a professor and chairs the Department of Computer and Information Sciences at the University of Delaware.
A letter of support from Biswjit Ray, an associate professor in the Department of Electrical and Computer Engineering at Colorado State University, noted that Bo Chen’s team has designed a novel approach that’s gaining increased attention in both high-impact publications and at top-tier cybersecurity conferences.
"Dr. Chen’s team has initiated a new research direction for secure data deletion."
Yang-Wai Chow, a researcher from the University of Wollongong in Australia who was not involved in Bo Chen and Niusen Chen’s project, said in a letter of support that their work has impacted and inspired his own endeavors. “I appreciate the research works from Dr. Chen’s group, which provided me with a strong foundation for advancing my research on PDE,” Chow said.
"Their research will significantly benefit billions of mobile device users in the world."
In this Michigan Tech News Q&A, Bo Chen and Niusen Chen reflect on their findings and their work together.
Q: You’re sitting next to someone on a plane or some other place where people strike up conversations. How do you describe your work?
BC: I have been working on cutting-edge security and privacy problems, safeguarding digital assets and protecting individuals’ privacy against malicious attacks.
NC: My Ph.D. dissertation focuses on enhancing data confidentiality in modern computing devices. It explores effective strategies for ensuring that deleted data cannot be recovered and protecting sensitive information when device owners are coerced by attackers. Additionally, my research extends to malware detection and defense, as well as security measures for connected and autonomous vehicles.
Q: How will your research benefit mobile device users in general?
BC: Our research aims to ensure the confidentiality of sensitive data stored in mobile computing devices, protecting user privacy. We have also worked on developing tools that allow users to restore their critical data upon being hacked by malware, safeguarding their digital assets.
NC: My research primarily benefits mobile device users by enhancing the security and privacy of their data. By developing methods to achieve secure deletion, users can confidently dispose of or recycle their devices without fear of their personal information being retrieved by unauthorized parties. Additionally, by exploring strategies to protect sensitive data under coercion scenarios, my research aims to safeguard user information in extreme situations, providing a higher level of security and peace of mind for everyday mobile device users.
Q: What are some specific impacts for institutions and people who deal with confidential information like medical and financial institutions?
BC: Our research can be broadly applied to safeguard sensitive information in critical departments such as medical and financial institutions. Compared to the traditional encryption techniques, our PDE design can provide an extra layer of confidentiality protection. This can ensure that critical medical and financial data can remain protected even if the attacker performs rubber-hose cryptanalysis (a euphemism for coerced extraction of data). In addition, our secure deletion design can ensure that sensitive medical and financial data can be completely sanitized upon turning obsolete, which is critically important for compliance with various data security regulations.
NC: For medical institutions, ensuring that deleted data — such as patient records — cannot be recovered helps comply with stringent data protection regulations like HIPAA. This enhances patient trust and safeguards sensitive health information against breaches. For financial institutions, my work on protecting sensitive data when device owners are coerced can prevent data leaks in scenarios involving threats or security breaches. By developing robust defense mechanisms, these institutions can better protect their clients’ financial data from unauthorized access, thus maintaining their reputation and adhering to financial privacy regulations.
Q: You hear people say that data never really goes away and can always be retrieved. There is a high demand for secure data deletion. How did you approach and work to develop irrecoverable deletion?
BC: We targeted a “full-stack” secure deletion design, which can sanitize remnants of sensitive data at all layers of a complicated computer system.
NC: Our research primarily addresses the secure removal of outdated sensitive data from flash memory, which is commonly used as external storage in mobile devices. Flash memory’s distinct characteristics lead to the generation of various data “remnants” even after data deletion. These remnants can potentially be exploited by adversaries to recover deleted data, thereby undermining the assurance of secure deletion. Through rigorous theoretical analysis and extensive experiments using real-world workloads, we identified “duplicates” — a specific type of data remnant that arises from the intrinsic operations (such as garbage collection, wear leveling and bad block management) of flash translation layer firmware. We have also developed the first secure deletion scheme that efficiently and effectively eliminates both the data and its duplicates from flash memory, thus achieving true secure deletion.
Q: What were some of the existing tools you worked with — and what tools needed to be invented?
BC: We mainly worked with open-sourced tools such as open-sourced firmware (OpenNFM) and file systems (EXT, NTFS, FAT). We developed various tools that can be used to hide sensitive data using PDE. We also developed tools that can be used to sanitize sensitive data at the lower-layer flash memory hardware.
NC: We employ the LPC-H3131, a programmable testbed designed for flash devices, as a primary resource in our research. Alongside this, we use Firefly and Raspberry Pi as host devices. By integrating LPC-H3131 with Firefly or Raspberry Pi, we can create prototypes that replicate the architecture of modern mobile devices. For the software aspect, we utilize IAR Embedded Workbench to compile our secure code.
Q: Tell me about the framework you developed. How does PDE protect the confidentiality of sensitive data and why was that important to include in a framework with secure data deletion?
BC: PDE allows the victim to deny the existence of sensitive data even if the victim is coerced by the adversary. This deniability property cannot be provided by traditional encryption mechanisms. Essentially, PDE allows the victim to disclose a decoy key to the adversary, preventing the adversary from knowing the existence of the actual secret key.
“PDE is designed to protect the confidentiality of the existing data while secure data deletion is designed to protect the confidentiality of the obsolete data. Together they form a complete framework for confidentiality protection which is long-term and regulation compliant.”

NC: We have developed three frameworks in this area. MobiWear is a PDE system design that is specific for wearable computing devices. CrossPDE is the first cross-layer mobile PDE system. HiPDS is a hardware-independent PDE system. PDE enhances data confidentiality by enabling users to deny the existence of encrypted data. It typically involves multiple layers or hidden volumes of encryption, allowing users to reveal less sensitive information while maintaining the secrecy of more critical data.
PDE is employed to safeguard data throughout its lifecycle. On the other hand, secure deletion is crucial for eliminating outdated or no longer needed data, preventing unauthorized access after its useful life. Incorporating both strategies in modern computing devices is essential, as it addresses comprehensive data security challenges. This dual approach ensures that sensitive information is shielded both during active use and upon its disposal, thereby fortifying the overall data protection framework in today’s digital environment.
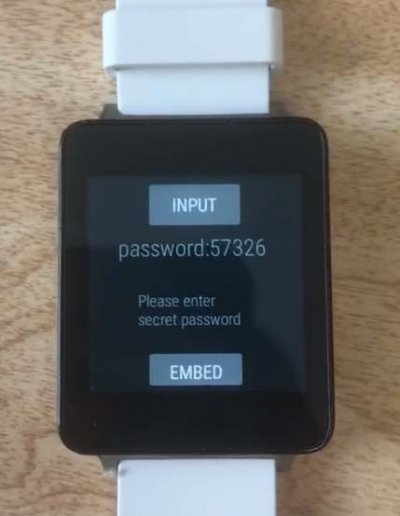
The prototype of the research team's PDE system built for the LG G watch lets users set both public and secret passwords differentiated by how they rotate the device. The secret password can be used to embed sensitive data stealthily into the innocent data. (Image credit: Bo and Niusen Chen)
Q: What were the biggest challenges and how did you meet them?
BC: There were a few major challenges. First, preventing the leak of sensitive data in the system memory is hard. We have addressed the challenge by incorporating the trusted execution environment, a hardware-level security feature built into processors of modern computer systems. Second, handling the leak of sensitive data in the storage system is hard due to the complicated design of a storage system in modern computing devices. We have intercepted multiple sublayers of the storage system, developing multiple novel techniques, which can be integrated into each unique storage sublayer.
NC: Our research is somewhat dependent on hardware, which can make setting up our environment challenging at times. For instance, when we initially utilized ARM TrustZone, I spent several days experimenting with various OS (operating system) versions to get it operational. Whenever I encountered issues that were beyond my ability to resolve, I typically scheduled meetings with Dr. Chen to strategize and find solutions.
Q: How did you get interested in this research? Why do you care about it?
BC: I have been working on data security research since I was a doctoral student. When I became a faculty member at Michigan Tech, I started to explore the unique technical challenges of data security faced in emerging mobile computing devices. This research is becoming more critical, as mobile computing devices are now extensively used to process personal and mission-critical data, while cyber attacks on these devices have significantly increased in recent years.
NC: I became interested after seeing how cyber attacks can affect everyone, from small businesses to big governments. I want to help find ways to stop these attacks and keep our information safe.
“I got into cybersecurity because it’s important for protecting our personal information and keeping our country safe as we use more technology.”

Q: This award is a team effort. Tell me more about your collaborators.
BC: Our collaborators include both faculty members and students from Wayne State University and the University of Delaware. Our collaborators have extensive expertise in memory protection, which is an essential component of our developed framework.
NC: Our research team comprises a diverse group of scholars, including three Ph.D. and two undergraduate students. We frequently hire master’s students as research assistants to enrich our team with fresh perspectives and additional expertise. Our team is also committed to building strong collaborative relationships, working closely with notable universities like Wayne State University and the University of Delaware. Such collaborations are vital, enhancing our research output and enabling a richer exchange of knowledge across institutions.
Q: How many years have you worked together? What was it like to work with each other? What did you learn from each other?
BC: We have been working together since fall 2018. I have enjoyed my collaboration with Niusen Chen, a smart, diligent and reliable student. Niusen has been excited with new technical challenges, and our research achievements would not be possible without his contributions. He will join a university in Wisconsin, and I am confident that he will be very successful as a faculty member and a cybersecurity researcher in his future career.
NC: I have been working with Dr. Chen for six years. Before entering the Ph.D. program, I had a limited background in computer security. Dr. Chen generously offered extensive advice and guidance, helping me deeply engage with the field. He is a committed professor, full of innovative ideas, and has provided invaluable suggestions regarding my career path.
In summary, Dr. Chen is not only a supportive mentor but also a genuinely nice person. I highly recommend that other students enroll in his classes and pursue research opportunities with him.
Q: Why did you come to Michigan Tech?
BC: I joined Michigan Tech in fall 2017 and was attracted by the supportive and collaborative environment for scientific research. I have been supported by multiple seed grants from the University, the College of Computing, the College of Business and the ICC, which provided me with the indispensable resources to boost my research and to secure various research grants from federal agencies such as the National Science Foundation.
NC: I chose Michigan Tech primarily for its outstanding programs, which are aligned with my career goals in technology and innovation. The location in Houghton, surrounded by natural beauty and outdoor activities, was also a major draw, providing a great balance between study and leisure. Moreover, the University’s focus on research and practical learning experiences was crucial in my decision, as it promised a hands-on approach that was essential for my professional development.
Q: Where and how have you been sharing your research with students?
BC: We have organized multiple events, such as the cybersecurity track of the Michigan Tech’s Women in Computer Science (Cybersecurity Track) Summer Youth Programs exploration and the GenCyber Summer Cybersecurity Camp. We also conducted the MTU Explore CSR Workshop for Undergraduates from Underrepresented Groups cybersecurity track. We have continuously hosted students from community colleges through the Michigan College and University Partnership (MiCUP) Scholars Program and given lectures to the new computer science undergraduate students in the CS1000 course. We delivered our research results in courses CS5740/4740 and CS5472. In addition, we continuously presented our research results in academic conferences and journals, and gave invited talks to other universities.

NC: We hosted numerous outreach activities to disseminate our research among students, including the ones Dr. Chen mentions, as well as sharing it at Michigan Tech Preview Day. Additionally, I integrated our research into the curriculum of CS4740/5740 as a special topics course for the spring 2024 semester.
Q: What’s next for you in your research endeavors?
BC: I plan to shift my research focus from security and privacy in embedded systems to that of critical cyber-physical systems. I’m also interested in securing critical systems in the post-quantum era.
NC: I will be joining another university as an assistant professor, where I will continue my work on addressing security vulnerabilities in the real world.
Q: Anything else you’d like to share?
BC: I would like to wish Niusen Chen a bright future career. I would also like to thank the Department of Computer Science, the College of Computing and College of Business, and the ICC. I offer special thanks to our sponsors, including the National Science Foundation and the U.S. National Security Agency.
NC: I would like to express my gratitude to Dr. Bo Chen for his continuous support and guidance throughout my Ph.D. journey and career. I am also thankful to my colleagues in our lab, including Josh Dafoe, Caleb Rother, Harsh Singh and Job Siyfor their collaboration and help. Additionally, I extend my thanks to the Department of Computer Science. Studying here has been a truly outstanding experience.
Michigan Technological University is an R1 public research university founded in 1885 in Houghton, and is home to nearly 7,500 students from more than 60 countries around the world. Consistently ranked among the best universities in the country for return on investment, Michigan's flagship technological university offers more than 120 undergraduate and graduate degree programs in science and technology, engineering, computing, forestry, business, health professions, humanities, mathematics, social sciences, and the arts. The rural campus is situated just miles from Lake Superior in Michigan's Upper Peninsula, offering year-round opportunities for outdoor adventure.





Comments